StegoCommand Datasheet 

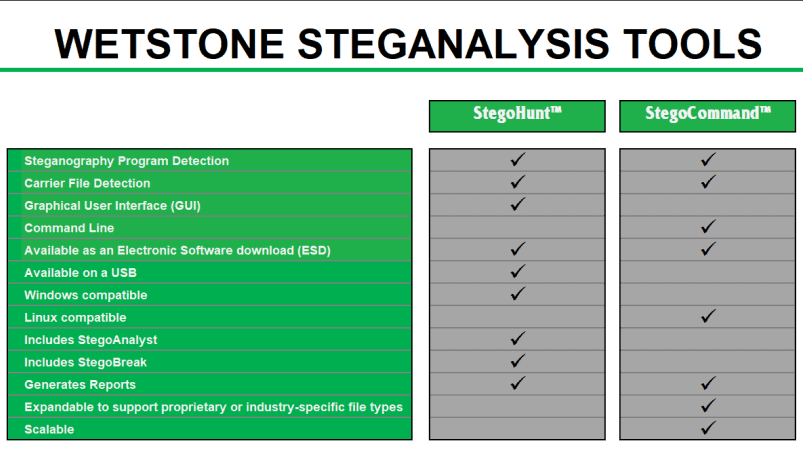
StegoCommand is a command line Linux application that scans specified directories containing files to examine, and generates a report for each scanned file. StegoCommand is simple to use and requires a minimal amount of technical knowledge. StegoCommand builds upon the capabilities of the industry-leading Steganography detection and steganalysis software tool, StegoHunt. Like its Windows-based predecessor, StegoCommand uses a collection of detection algorithms to quickly identify the presence of steganography in suspect carrier files.
Use cases for StegoCommand include: acceptable use policy enforcement, forensic investigations, data breach response, data leak analysis, insider threat identification, and mobile device examination.
STEGANOGRAPHY DETECTION ACROSS THE BOARD
StegoCommand supports several “out-of-the-box” file types for scanning for the presence of steganography. In addition to the “out-of-the-box” file types offered, the WetStone Technologies research and development team can work directly with a customer to expand the capabilities to scan for steganography in unique, custom, proprietary or industry-specific file types.
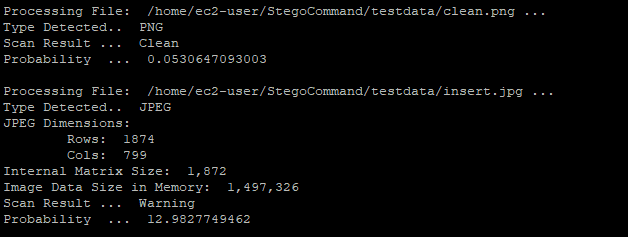
StegoCommand has the ability to traverse an unlimited number of nested archive files. Nested archives are often used in an attempt to conceal the presence of data hiding. With StegoCommand, users can be assured that all files in an archive file will be analyzed for the presence of hidden data.
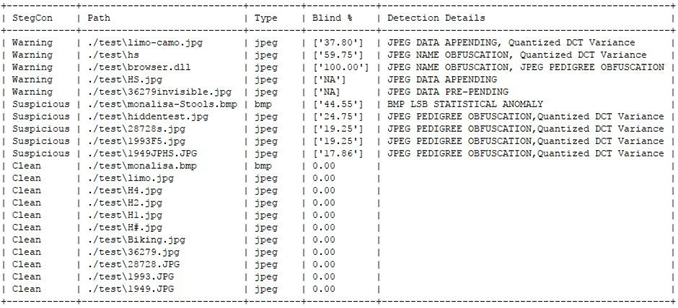
FEATURES OF STEGOCOMMAND
StegoCommand detects and provides comprehensive reports on:
- statistical anomalies
- structural anomalies
- the presence of misplaced binary or UTF-8 data
- data appending
- data prepending
- file name obfuscation
- the presence of unusual Unicode data
- Comprehensive reporting
StegoCommand is:
- Easily deployed in either on-premise or cloud-based environments
- Scalable to support analysis of very large files and very large data repositories
- Invoked via a command prompt or PowerShell
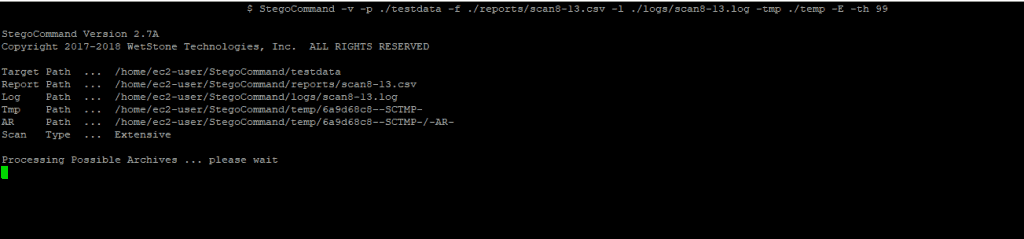
FILE TYPES SUPPORTED
- JPEG
- GIF
- BMP
- PNG
- ASCII (txt, csv, xml and html)
- Archive Files (includes but not limited to ZIP, TAR, JAR, APK, BZ2)
- HDF5
- NetCDF4
- BUFR
- NEXRAD
- HDF4
- HSD (Himawari)
SUPPORTED PLATFORMS
- Ubuntu
- Red Hat Enterprise Linux version 7
WetStone Technologies can work directly with a customer to support additional operating systems.
SYSTEM REQUIREMENTS
Computer system or virtual machine must meet or exceed the minimum requirements of 4GB RAM and 4 Core Processor.