Gargoyle Investigator LE Datasheet 
- Gargoyle Investigator LE is a supplemental tool to the popular Gargoyle Investigator MP, in use by forensic labs, law enforcement, field investigators, private investigators, and incident response teams, world-wide.
- Available to qualified law-enforcement professionals, Gargoyle Investigator LE delivers automated search and classification of child sexual abuse material (CSAM).
- Gargoyle Investigator LE supports a wide variety of image types and the carving of images from many file types, including Microsoft Office, Adobe Acrobat, and archive formats.
- Comprehensive reporting is an essential feature of Gargoyle Investigator LE. Reports are available in html, pdf and csv formats.

Gargoyle Investigator LE is a software tool that provides investigators the ability to conduct automated in-depth search and analysis of live and imaged systems and detect the presence of exploitative material and child sexual abuse material (CSAM).
Utilizing Project VIC and PhotoDNA technology, Gargoyle Investigator LE analyzes media on a system and carves multimedia files out of other files—such as Word documents, PDFs, etc.

Powered by Project VIC and using PhotoDNA, Gargoyle Investigator LE performs fast and accurate identification of exploitative media. Files are scanned based on scope set by the user. The source of files can be a directory, mounted disk image, or a disk volume.
Gargoyle LE utilizes Project VIC, a standards-based protocol for the exchange of exploitation hashes, domestically and internationally, without having to touch or manipulate the data. Gargoyle LE also utilizes PhotoDNA technology, which provides transformations on an image to calculate its PhotoDNA signature, or hash, which can be compared to another image. This is used to find other copies of a given image, even if the image has been altered. Detections of such media are captured in the scan report, with blurred, categorized file information presented for the investigator.
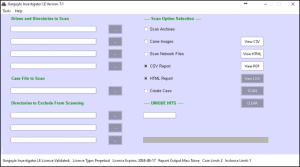
Gargoyle LE provides comprehensive reporting in both HTML , PDF and CSV formats for use as digital evidence. Reports are generated in HTML to present the data to the investigator in an easy-to-navigate format.

FEATURES OF GARGOYLE INVESTIGATOR™ LE
- Available to qualified law enforcement engaged in CSAM investigations
- Automated search, identification and categorization of CSAM images
- Comprehensive reporting
- Compatible with a variety of Windows desktop platforms:
- Windows 7
- Windows 8
- Windows 8.1
- Windows 10
- Compatible with a variety of Windows Server platforms:
- Windows Server 2008 and 2008 R2
- Windows Server 2012 and 2012 R2
- Windows Server 2016
DELIVERABLE
- Electronic Software Download (ESD) of Gargoyle LE
- Customer support portal account
- Software maintenance
LICENSING
- A license of Gargoyle Investigator LE is provided at no additional cost to eligible Law Enforcement customers who have an active license and support entitlement for Gargoyle Investigator MP.
- Gargoyle Investigator LE is a term license and entitlement coterminates with your support agreement if you have a perpetual license to Gargoyle Investigator MP or at the end of your subscription period if you have a Gargoyle Investigator MP term license.
- ESD: Electronic software download for use on a single system. Available as a perpetual or subscription license. Not transferable. Basic license is 2 cores, additional core licensing available.